SCCM & Sundry
Friday, June 10, 2016
Migration to TinyPress
I'll be moving my blog over to TinyPress. My new blog can be found here: https://dansonnenburg.github.io/
Thursday, March 24, 2016
Dell Latitude E5570 Bitlocker recovery problem
We
recently discovered a problem with Bitlocker on the Dell Latitude E5570
laptops, that after enabling bitlocker (we use MBAM), the computer prompts for
a recovery key after every reboot. It turns out this is a problem with
the Dell BIOS which is repaired through a BIOS update, though it has been noted
that running in UEFI mode may fix this problem as well. There is a nice
discussion in this issue here: http://en.community.dell.com/support-forums/laptop/f/3518/t/19674757?pi41097=1
The
root-cause of this problem is an issue with the default BIOS version on E5570,
E5470, and E7270s. Dell released a BIOS fix for this on March 16th.
To repair,
do the following:
1.
Be sure that you are plugged into a power source.
2.
Install the BIOS update, located here: http://www.dell.com/support/home/us/en/04/product-support/product/latitude-e5570-laptop/drivers/advanced
3.
After reboot you will be prompted to suspend and resume
bitlocker, press enter.
4.
Enter the bitlocker recovery key using the bitlocker help
desk portal.
5.
From an elevated command prompt
·
type: Manage-bde.exe –protectors –disable c:
·
Manage-bde.exe –protectors –enable c:
6.
Reboot the computer to ensure that the problem has been
resolved.
Friday, August 21, 2015
Custom log size in WinPE during Task Sequences
Do you hate doing things manually? Do you hate reading through forums and blogs to solve problems? I do, that's why I write scripts to solve problems. They are concise and usually fairly readable. I referenced Niall Brady's blog: http://www.windows-noob.com/forums/index.php?/topic/11071-how-can-i-increase-the-smstslog-file-size-for-pxe-based-os-deployments-using-system-center-2012-r2-configuration-manager/ for the solution, so thank you very much Niall! I have difficulty remembering the individual steps at times, so I like to script it out as a quick reference and to create a repeatable process. In this case, I wanted to increase the log size while in WinPE during Operating System Deployment (OSD) task sequences. If you want the specific detail, please refer to Niall's blog, otherwise modify the variables in the script to suit the needs of your environment. Just change the variables, run the script, and update your boot images on the DPs and you're all set!
Here's a link to the script: http://1drv.ms/1U58mzr
Here's a link to the script: http://1drv.ms/1U58mzr
Thursday, June 4, 2015
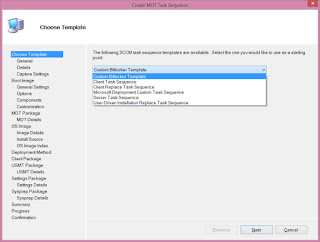
Creating ConfigMgr-MDT Task Sequence Templates
Ever wondered how to create custom SCCM templates when MDT is integrated? Wonder no further, I have written a little script that should make the process seamless.
All you need to do is customize the variables in the script to your preferences and provide a reference task sequence to create your template. I saved my templates here on my local machine: "C:\Program Files\Microsoft Deployment Toolkit\SCCM\" so that the template was immediately available for use in the ConfigMgr console.
To access the new template, simply right click on Task Sequences in the console and select "Create MDT Task Sequence."
Good luck!
The script can be found here: http://1drv.ms/1dPFhuk
All you need to do is customize the variables in the script to your preferences and provide a reference task sequence to create your template. I saved my templates here on my local machine: "C:\Program Files\Microsoft Deployment Toolkit\SCCM\" so that the template was immediately available for use in the ConfigMgr console.
To access the new template, simply right click on Task Sequences in the console and select "Create MDT Task Sequence."
Then simply select your new task sequence, mine is called "Custom Bitlocker Template".
Good luck!
The script can be found here: http://1drv.ms/1dPFhuk
Friday, May 8, 2015
Windows 8.1 De-duplication, Mounting VDHX, and Symlinking...oh my
First of all, I realize that this isn't an ideal setup for everyone, but for my home lab I found that this worked pretty well. My dilemma was such: I had a home lab setup on my desktop PC running Windows 8.1 with Hyper-V on a 500GB SSD but was running out of room quickly. De-dup is not supported on system or boot volumes, so I had to come up with a different solution.
I borrowed much (most) from Johan Arwidmark over at deploymentresearch.com: http://deploymentresearch.com/Research/Post/406/Beyond-Zip-How-to-store-183-GB-of-VMs-in-a-16-GB-file-using-PowerShell and Teh Wei King's System Center Blog: https://weikingteh.wordpress.com/2013/01/15/how-to-enable-data-deduplication-in-windows-8/
Here's a brief outline of what I'll cover here:
I borrowed much (most) from Johan Arwidmark over at deploymentresearch.com: http://deploymentresearch.com/Research/Post/406/Beyond-Zip-How-to-store-183-GB-of-VMs-in-a-16-GB-file-using-PowerShell and Teh Wei King's System Center Blog: https://weikingteh.wordpress.com/2013/01/15/how-to-enable-data-deduplication-in-windows-8/
Here's a brief outline of what I'll cover here:
- Create VHDX file, mount it to a drive letter, copy files.
- Enable Dedup on Windows 8.1.
- Dedup the VHDX volume.
- Create symlinks to the new location.
- Automatically mount VHDX files on boot.
It should be immediately pointed out that de-dup is not officially supported in Windows 8.1, however, when it works, it's really dang awesome! Additionally, symlinking is really not necessary at all, but it is really nice if you don't want to re-install applications, re-link paths to VHDXs, etc.
- Create VHDX file, mount it to a drive letter, copy files. Create the VHDX file using Create-VHDX.ps1. It will automatically mount the VHDX to a drive letter. After mounted, copy your VMs, files, apps, etc. to the new drive.
- Enable Dedup on Windows 8.1. First, grab the CAB files to enable the features in Windows 8.1. Make sure you copy the CAB files to the directory that you plan on running Enable-Win81Dedup.ps1 from or you'll need to specify the full paths to the CABs.
- Dedup the VHDX volume using Dedup-VHDX.ps1. You can check to see how we did by running a Get-DedupStatus command.
- Create symlinks by specifying the link and target directories with New-SymbolicLink.ps1.
- Automatically mount VHDX files on boot. There are at least a few ways to mount the VHDX on boot, however I found it difficult to consistently get the same drive letter, which was important since I wanted to create symlinks, so I chose to implement using a scheduled task and diskpart. You can create the scheduled task to mount the vhdx on boot by running Map-VhdxOnBoot.ps1.
Okay that's it! We're done! I hope you found this to be an useful exercise in how these somewhat unrelated capabilities can be paired together in an interesting way.
You can grab all of the scripts referenced in this article from here: http://1drv.ms/1zRejwj and the CAB files for enabling the dedup features can be found here: http://1drv.ms/1zReszA
Thursday, October 2, 2014
Backup and Restore a WIM from WinPE using DISM
Backup an image
- Boot from WinPE media.
- Determine the drive letter to be captured. This is typically C:,D:, or E:, but it can vary depending on which devices are connected to the system.
- There are a few choices for where to back up the image, but my preference is to back it up to a network drive. To do this, run the following command:
- Net use Z: \\<ServerName>\<DestinationPath>\
- You should see “The command completed successfully” if it works correctly. Remember, you need to have write permissions to this directory in order to save the image to it, so you should be prompted for credentials to connect to the share.
- DISM.exe should already be in the path environment variable in WinPE 5.0, so you can call the DISM executable from pretty much anywhere.
- DISM.exe /Capture-Image /ImageFile:Z:\capture.wim /CaptureDir:E:\
- Where Z: is the path to which you want to save the image and E: is the path to the partition with Windows installed.
- If the drive contains much data, it will take an amount of time proportional the amount of data and the throughput of your network, USB, or eSATA connection. Be patient
To restore an image to a new machine or a new drive, it is a
very similar process, only the command in step 4 really changes.
- Boot from WinPE media.
- Determine the drive letter to restore the image. This is typically C:,D:, or E:, but it can vary depending on which devices are connected to the system.
- If you used a network path to backup your image, you must re-map the drive again. To do this, run the following command.
- Net use Z: \\<ServerName>\<DestinationPath>\
- You should see “The command completed successfully” if it works correctly. Remember, you need to have write permissions to this directory in order to save the image to it, so you should be prompted for credentials to connect to the share.
- DISM.exe should already be in the path environment variable in WinPE 5.0, so you can call the DISM executable from pretty much anywhere.
- DISM.exe /Apply-Image /ImageFile:Z:\install.wim /Index:1 /ApplyDir:E:\
- Where Z: is the path where the backup image is stored and E: is the path of the partition to restore the image.
- If the image contains much data, it will take an amount of time proportional the amount of data and the throughput of your network, USB, or eSATA connection. Be patient!
Wednesday, October 1, 2014
Create a New AD and SCCM 2012 User Collection with PowerShell
Function New-SCCMUserCollection {
PARAM (
[Parameter(Mandatory = $true)] $ADCollectionName,
[Parameter(Mandatory = $true)] $CMCollectionName,
$limitingCollection = "All Users",
# Customize the $path appropriately for your environment.
$path = "OU=Application Deployment,OU=Groups,DC=<YourDomain>,DC=<YourNamespace>",
$description = "Application Deployment Group",
# Customize your domain name in the query.
$queryExpression = "select SMS_R_USER.ResourceID,SMS_R_USER.ResourceType,SMS_R_USER.Name,SMS_R_USER.UniqueUserName,SMS_R_USER.WindowsNTDomain from SMS_R_User where SMS_R_User.SecurityGroupName = '<YourDomain>\\$($ADCollectionName)'",
$ServerName = "<YourServerName>",
$SiteCode = "<YourSiteCode"
)
# Get a reference object for grabbing the RefreshSchedule property
# Use an existing collection as a template to replicate the RefreshSchedule.
$refreshSchedule = (Get-CMDeviceCollection -Name "7zip").RefreshSchedule[0]
$ruleName = $CMCollectionName
# Create AD Security Group
New-ADGroup -Name $ADCollectionName -SamAccountName $ADCollectionName -GroupCategory Security -GroupScope Universal -DisplayName $ADCollectionName -Path $path -Description $description -Verbose
# Create SCCM Collection
New-CMUserCollection -Name $CMCollectionName -LimitingCollectionName $limitingCollection -Verbose -RefreshSchedule $refreshSchedule -RefreshType 2
# Add collection rule
$CollectionName = Get-CMUserCollection -Name $CMCollectionName
Add-CMUserCollectionQueryMembershipRule -CollectionId $CollectionName.CollectionID -RuleName $ruleName -QueryExpression $queryExpression -Verbose
}
# Import the Configuration Manager 2012 Module
Import-Module "C:\Program Files (x86)\ConfigMgr2012\bin\ConfigurationManager.psd1"
# Set location the primary site code
Set-Location <YourSiteCode>:
Import-Module ActiveDirectory
# Edit this variable to reflect the desired AD Security Group Names
$ADCollectionName = "Test User Collection"
# Do not edit this variable unless it is a special circumstance.
$CMCollectionName = "$ADCollectionName - User"
# Usage: New-SCCMUserCollection -ADCollectionName $ADCollectionName -CMCollectionName $CMCollectionName
PARAM (
[Parameter(Mandatory = $true)] $ADCollectionName,
[Parameter(Mandatory = $true)] $CMCollectionName,
$limitingCollection = "All Users",
# Customize the $path appropriately for your environment.
$path = "OU=Application Deployment,OU=Groups,DC=<YourDomain>,DC=<YourNamespace>",
$description = "Application Deployment Group",
# Customize your domain name in the query.
$queryExpression = "select SMS_R_USER.ResourceID,SMS_R_USER.ResourceType,SMS_R_USER.Name,SMS_R_USER.UniqueUserName,SMS_R_USER.WindowsNTDomain from SMS_R_User where SMS_R_User.SecurityGroupName = '<YourDomain>\\$($ADCollectionName)'",
$ServerName = "<YourServerName>",
$SiteCode = "<YourSiteCode"
)
# Get a reference object for grabbing the RefreshSchedule property
# Use an existing collection as a template to replicate the RefreshSchedule.
$refreshSchedule = (Get-CMDeviceCollection -Name "7zip").RefreshSchedule[0]
$ruleName = $CMCollectionName
# Create AD Security Group
New-ADGroup -Name $ADCollectionName -SamAccountName $ADCollectionName -GroupCategory Security -GroupScope Universal -DisplayName $ADCollectionName -Path $path -Description $description -Verbose
# Create SCCM Collection
New-CMUserCollection -Name $CMCollectionName -LimitingCollectionName $limitingCollection -Verbose -RefreshSchedule $refreshSchedule -RefreshType 2
# Add collection rule
$CollectionName = Get-CMUserCollection -Name $CMCollectionName
Add-CMUserCollectionQueryMembershipRule -CollectionId $CollectionName.CollectionID -RuleName $ruleName -QueryExpression $queryExpression -Verbose
}
# Import the Configuration Manager 2012 Module
Import-Module "C:\Program Files (x86)\ConfigMgr2012\bin\ConfigurationManager.psd1"
# Set location the primary site code
Set-Location <YourSiteCode>:
Import-Module ActiveDirectory
# Edit this variable to reflect the desired AD Security Group Names
$ADCollectionName = "Test User Collection"
# Do not edit this variable unless it is a special circumstance.
$CMCollectionName = "$ADCollectionName - User"
# Usage: New-SCCMUserCollection -ADCollectionName $ADCollectionName -CMCollectionName $CMCollectionName
Subscribe to:
Comments (Atom)